How to Use SIEM Effectively?

In the last article, we talked about the top 5 SIEM reports and how you can generate them on the Logsign SIEM platform. We covered reports related to user accounts, file access, user/group changes, threats, and attacks. This article will show how you can effectively use the Logsign SIEM platform along the lines of the most popular use cases. A use case is defined as a series of actions or events between a system and a user that achieve a particular goal.
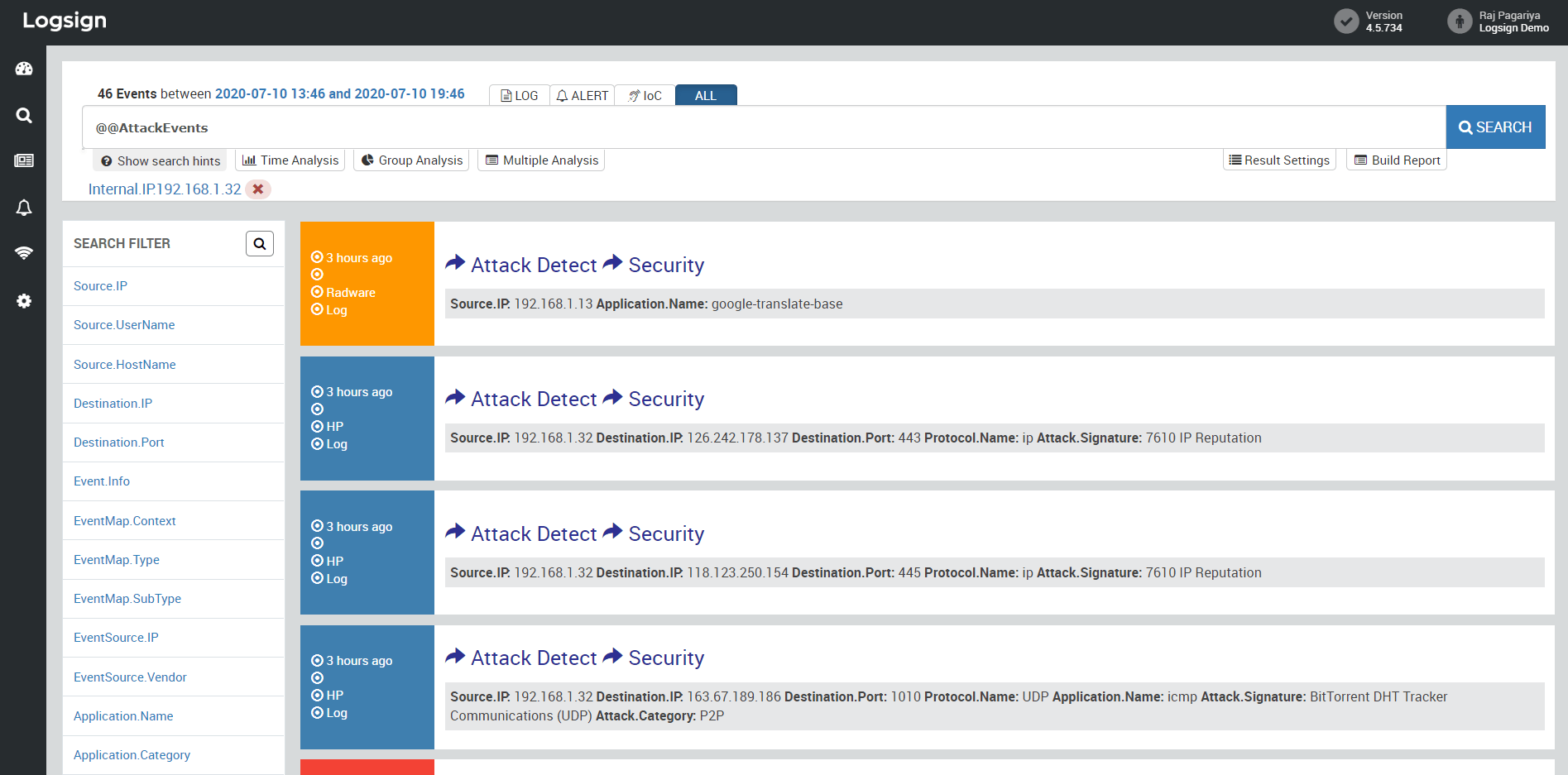
A Verizon Data Breach Investigation report has found that three out of the top five reasons behind security incidents are somehow related to insider threats. So often, we have seen that organizations focus extensively on defending against external threats while they miss out on implementing adequate measures for insider threats. Logsign SIEM uses its inbuilt alert rules along with the correlation motor to identify:
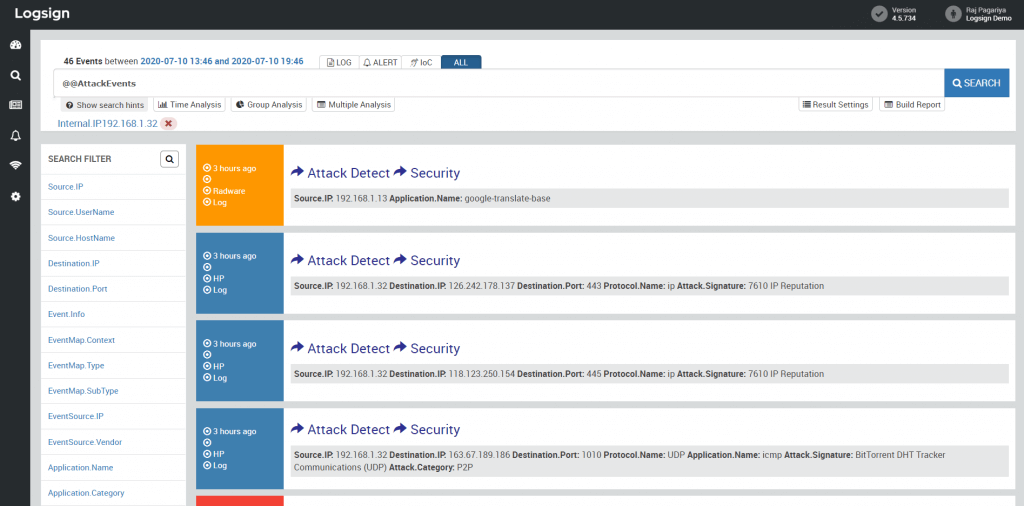
Figure 1: Attack activity detected for an internal IP address
Traditional signature-based malware detection has been proven inefficient time and again. Previously unknown malware have been able to get through the defences of signature-based detection tools. A successful malware attack may cause harm to organizational data, and the extent of loss is not only limited to financial and reputational damages. Without a doubt, detecting and removing malware is complicated, but Logsign SIEM combines threat intelligence (TI) feeds with existing correlation rules to create alerts and generate reports. This correlation utilizes log data for detecting malware and tags various parties as an attacker, victim, and suspicious. Logsign SIEM platform performs behaviour analysis to track the activities of the attacker, and it sends alerts to your team. To prevent malware from communicating with its C&C server, relevant deny rules are written by using API sharing on Palo Alto, Checkpoint, and FortiGate firewalls.
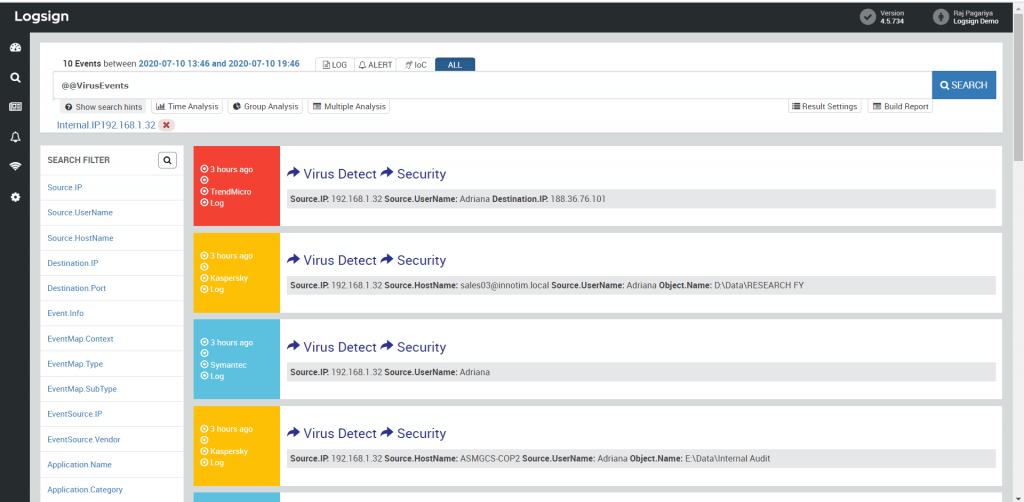
Figure 2: Malware detection on Logsign SIEM
A zero-day attack exploits a vulnerability or weakness in an application or program that are not known previously. Just like we discussed for malware, traditional tools based on signature detection are rendered useless to defend against zero-day attacks. Similar to what we discussed in the last section, Logsign SIEM uses correlation rules and TI feeds along with combining log data from DNS server, IPS, process events, proxy server, and endpoint protection platform (EPP) source logs.
File servers like Windows allow multiple users to access storage space and files available therein. In a company with hundreds of employees, it is difficult to prevent unauthorized access by merely monitoring authorization requests. Responsible individuals, generally managers, require authorization reports of all such shared folders to find if any user has more than required access level. For hundreds of users, this process may be futile and time-consuming.
Using correlation rules in sync with access control and process creation logs, Logsign SIEM effortlessly tracks access activities on the shared folders on Windows systems. After behavioural analysis, Logsign SIEM tags relevant parties as an attacker, victim, and suspicious. Once detected, the SIEM platform sends alerts through email and SMS.
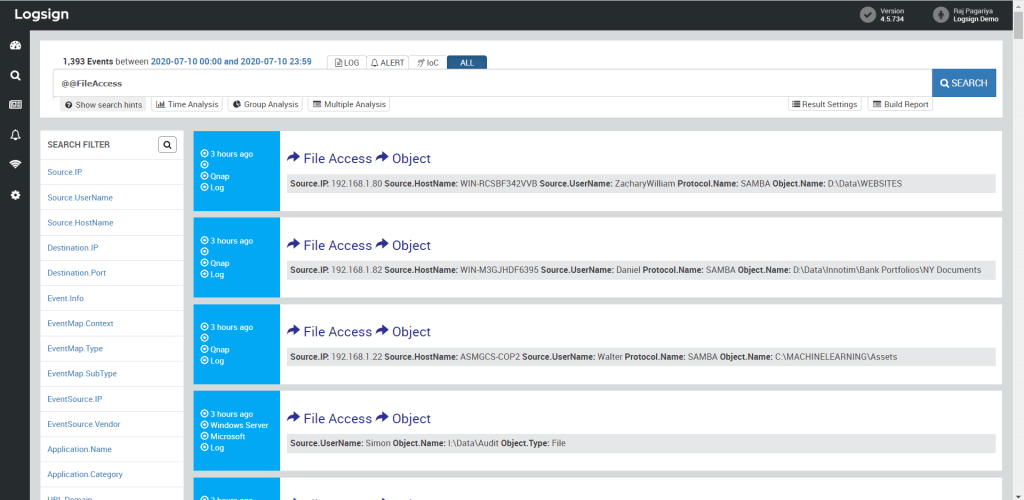
Figure 3: File access events on Logsign SIEM
With effective password cracking tools, brute force attacks pose a significant risk to organizations. An organization shall be able to detect suspicious login attempts and changes made in system files before any large-scale damage. Brute force attacks involve using automated tools to break into target user accounts. By grouping important parameters such as frequency of login attempts, username, and IP address, the SIEM platform creates a security incident after threshold limits are crossed. Logsign SIEM uses behaviour analysis to reel out false positives and mark a party as the attacker. Accordingly, it notifies your team through emails and SMS.
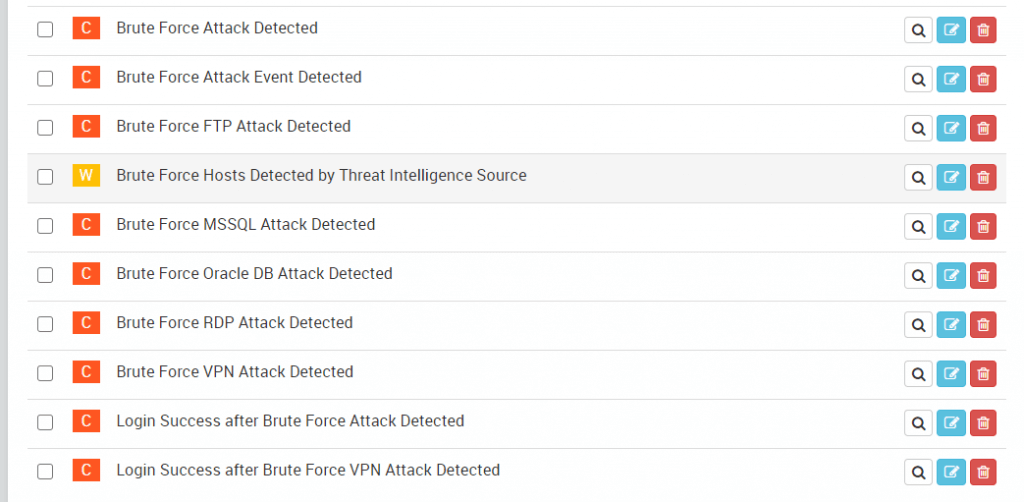
Figure 4: Some of the rules for detecting Brute Force Attack on Logsign platform
Have you been able to derive benefits from these use cases on Logsign SIEM platform? If not, get in touch with our Support team today!