What is Threat Intelligence?


Use of cyber threat intelligence in a security operations center is an essential part to attain a strong security posture. Therefore, since cyber threat intelligence is that important, understanding the general framework is also vital. Gartner defines threat intelligence quite comprehensively whereas:
“Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject's response to that menace or hazard.”
Thus, it can be roughly summarized as gathering various information about numerous threat actors to either deal with them on-spot or to implement a proactive threat management method. In terms of cyber security, they are the main point of departure to handle cyber attacks accordingly. Yet, they shouldn’t be narrowed down merely to raw data.
Threat intelligence is an end-product of what’s called threat intelligence cycle (TIC). TIC consists of 6 steps to process the raw data. The steps are: Direction, Collection, Processing, Analysis, Dissemination, Feedback.
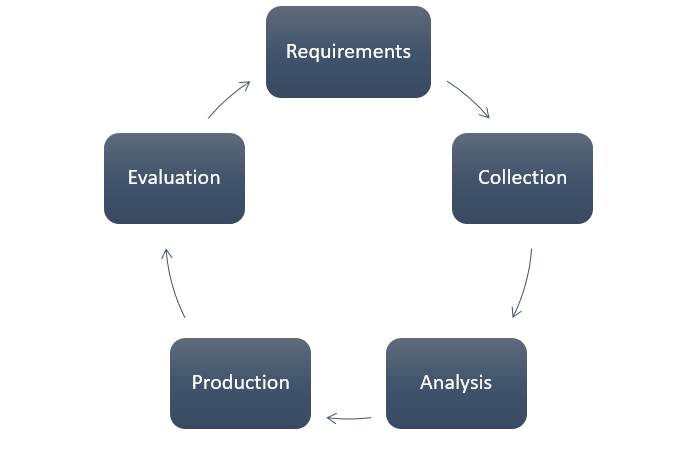
After moving through all of the steps, data becomes available to be utilized in various ways. Thus, it transforms into actionable threat data, that is also called Threat Intelligence Feed. Security teams operate on these feeds to combat a potential threat or a real-time one. However, unsurprisingly, analysts have to handle hundreds and thousands of threat intelligence feeds daily and this causes bottlenecks one after another and inefficiencies at the same time.
There are three types of threat intelligence that differ in accordance with their various attributes.
To begin with, there is strategic threat intelligence that provides high-level information. According to this article, they are suitable for long-term use and contain an important amount of data. In accordance with that, it especially covers topics that might be impactful for possible business decisions. Thus, broader topics and opportunities that might have an influence on the threat landscape. They are mainly extracted from open sources like white papers or reports which are within the reach of everyone.
Moving on, there are tactical TIs that are mainly concerned about tactics, techniques and procedures of threat actors. As the name states, they are targeting the technical audience like security analysts and allow them to increase their expertise on handling attacks or the methods that attackers predominantly use. IT managers or Security Operation Center SOC managers often handle this type of threat intelligence. They are mainly collected from malware or incident reports and raw data are often enriched through being crossed by this type of TI.

Finally, there is technical TI that generally includes low-level information attained through extensive searches or past experiences. They aim to collect information about several sources like phishing or IP addresses. They provide valuable intelligence to deal with attacks more resiliently.
In order to answer this one, another question arises: how to move security operations forward to handle the constant flow of threat intelligence? Luckily, tools like SIEM or SOAR constitute an answer with their extensive scope of tactics, techniques and procedure. They handle the threat intelligence prospectively, retrospectively or transiently. Being able to enrich the data in a detailed manner is deeply linked with automation, visualisation and responsiveness.
For example, these tools are able to perform threat hunting thanks to the threat intelligence they process. Cyber threat hunting and threat hunters strengthen the security posture of organizations due to it’s proactive nature. Assessing the TI data carefully, threat hunting foresights negative scenarios before they happen. Thus, they conduct proactive risk management that is quite crucial to protect sensitive information.
In terms of security measures, SOAR tools handle advanced threats through incident response mechanisms extracted by threat intelligence feeds. Keeping track of recurring incidents and their TI data and automatically solving them through machine learning is also what security tools are able to do. This is both linked with automation and visualisation that enables it to handle TI data accordingly.
In addition, they can deal with malicious software by enriching the TI data with various sources. This is the part where responsiveness steps in. In the end, managing TI accordingly provides organizations to prioritize security risks from different sources in a quick manner.
In the end, SOC tools like SIEM and SOAR enable organizations to handle TI data with much more precision and effectiveness. This way, the workflows of security analysts are disburdened and a further level of efficiency is attained. Following all of these, a stronger cyber security posture is naturally attained.
Threat intelligence is the essence of security operations. They are quite instrumental for dealing with malicious attacks and strengthening the security network of organizations. They are processed and enriched through various sources and steps to be utilized by analysts.
There are three types of TI that answer different demands. Yet, no matter how differentiated they are, they carry an important amount of information to be helpful to analysts.
However, analysts are generally burdened with these TI piling up day by day. Thus, SOC tools like SOAR and SIEM are essential to handle TI data accordingly.