Security Information and Event Management (SIEM)
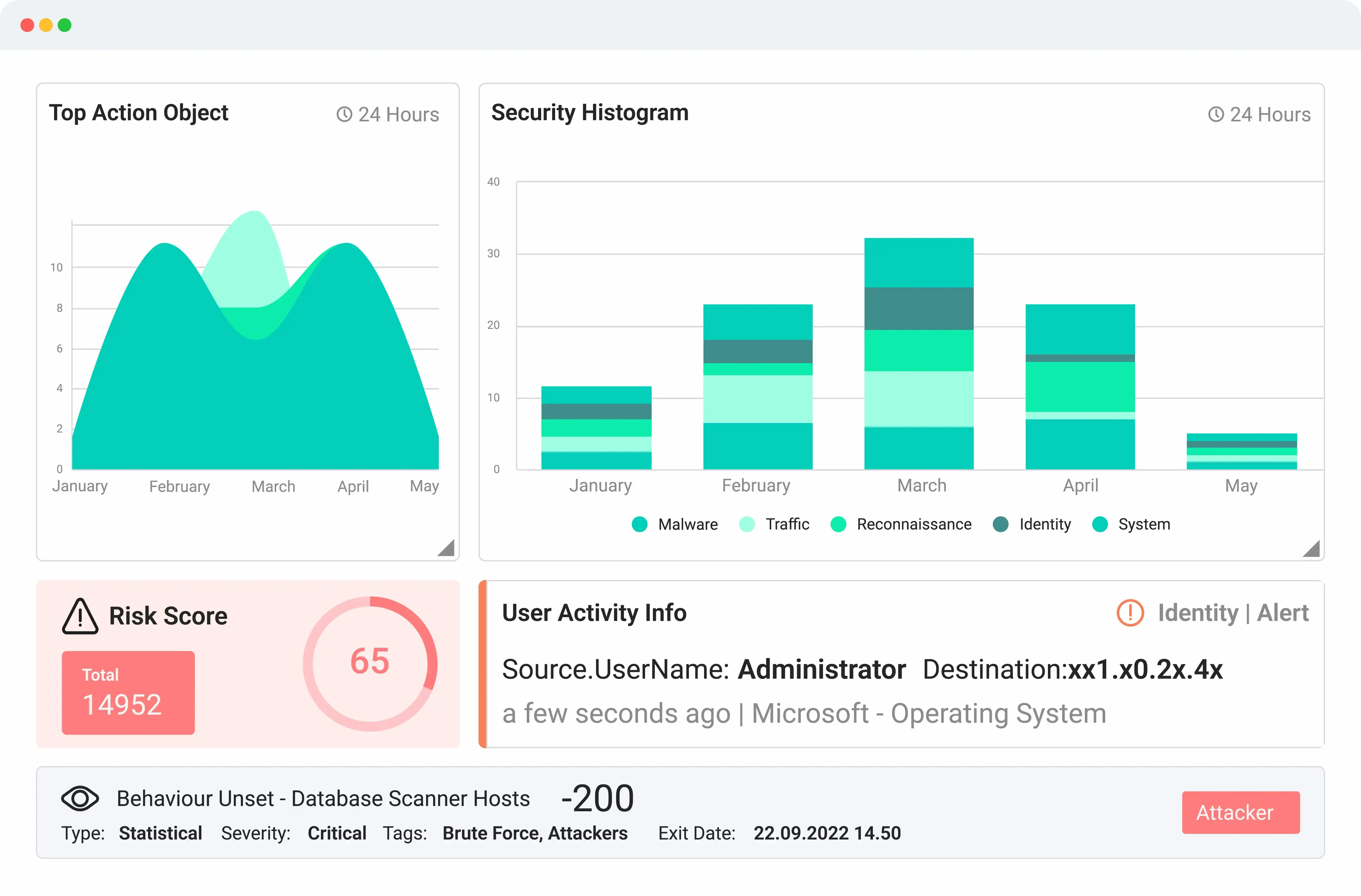
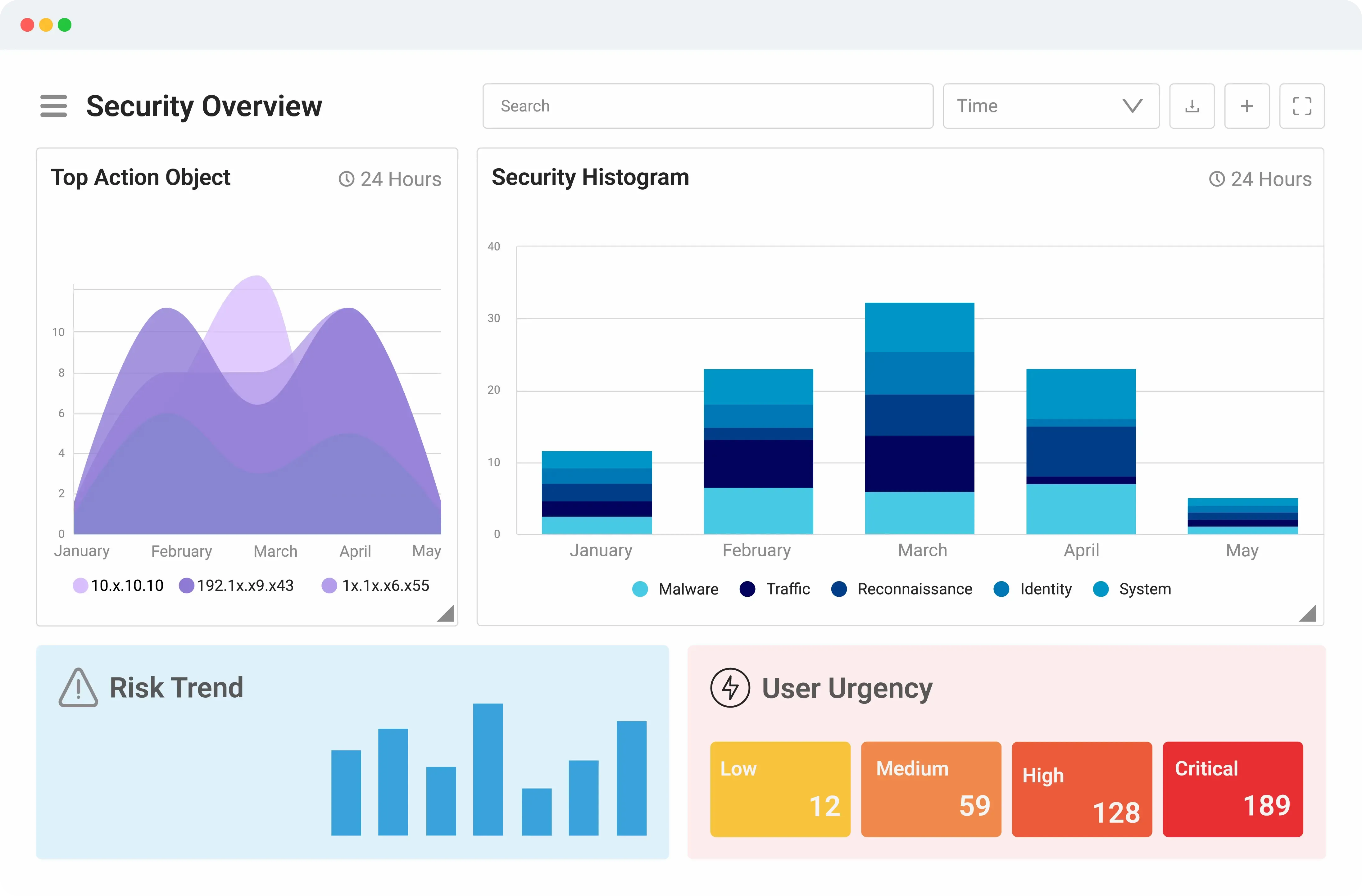
Logsign Unified SO platform offers you a recognised next-gen Security Information and Event Management (SIEM) solution. Create your own data lake, collect, investigate, detect and respond to cyber threats easily. It’s much more than a centralized event log management tool, designed for scaling, a vast volume of data collection and storage.
Threat Intelligence (TI)
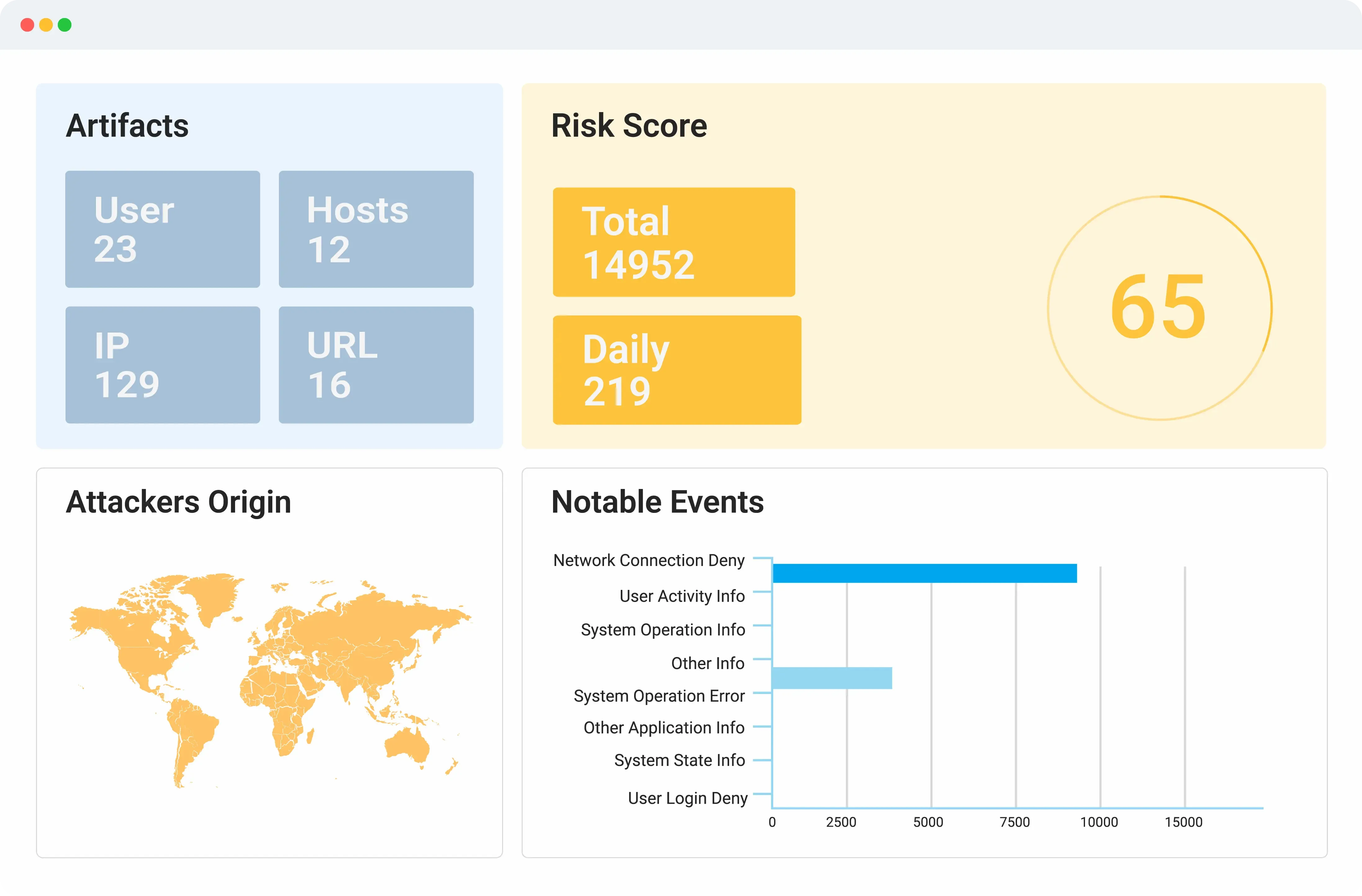
Logsign Unified SO platform rapidly investigates hidden cyber threats, IOCs, and suspicious attack vectors by combining global threat intelligence data. It also uses internal threat source feeds to risk prioritisation. Ensuring constant preparedness for potential threats such as powershell, zero-day or brute force attacks.
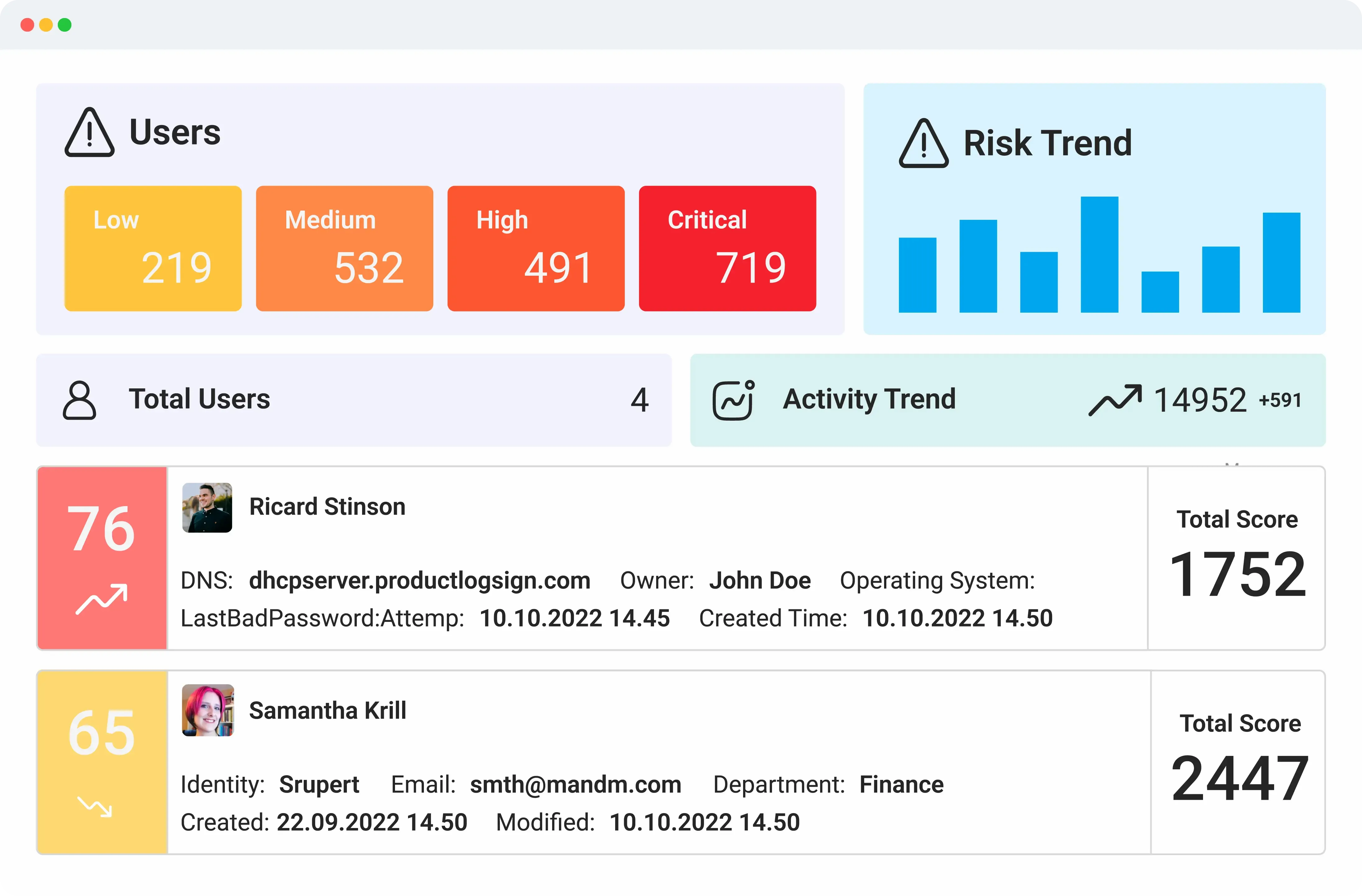
User and Entity Behavior Analytics (UEBA)
Logsign Unified SO platform’s UEBA capabilities analyses specific threat data to determine whether certain types of behaviour represent a cybersecurity threat including insider threats. Uses advanced analytics to collect and analyse data related to assets and identity.
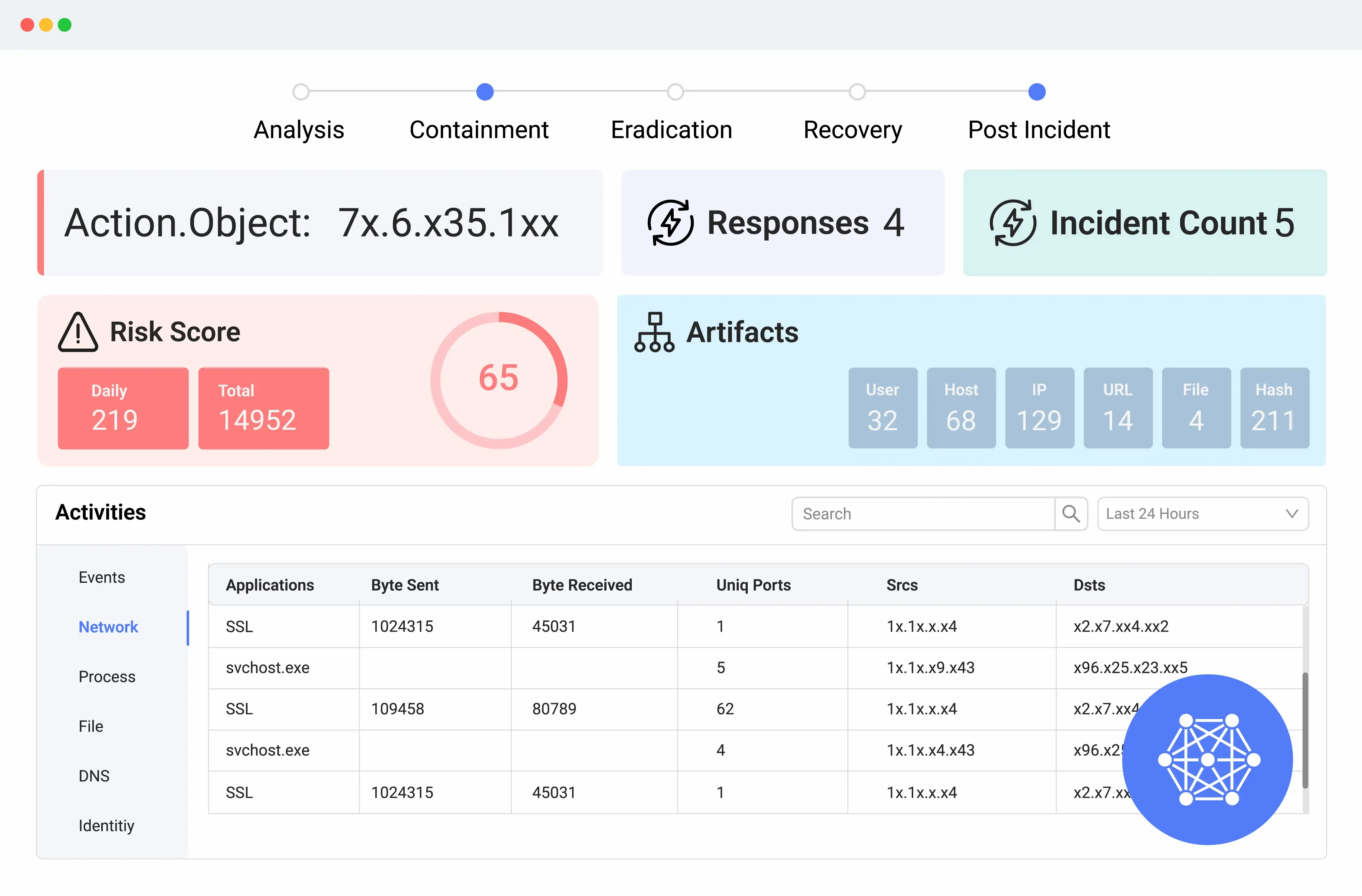
Automated Incident Detection, Investigation, and Response (TDIR)
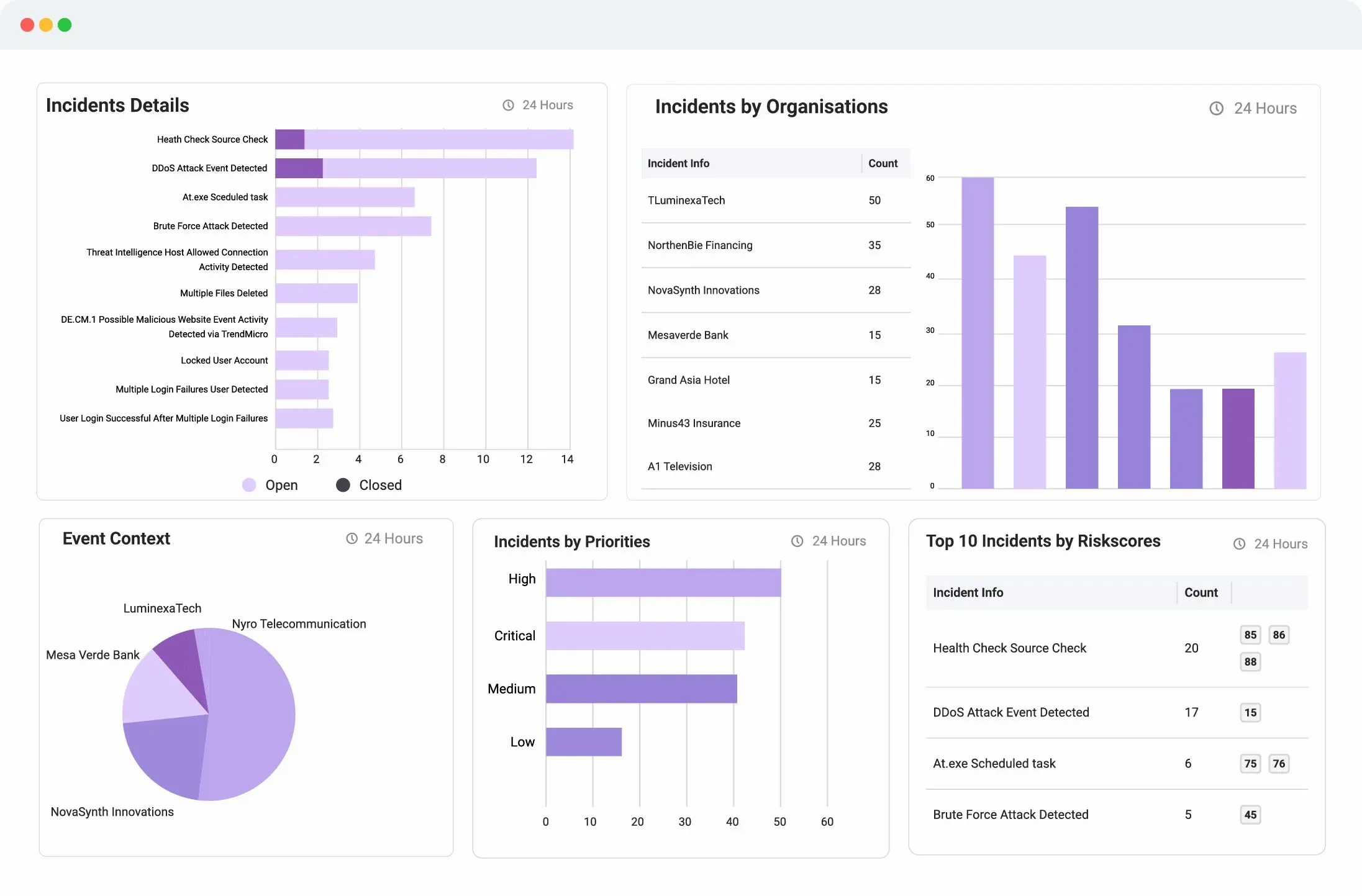
Logsign Unified SO platform offers your computer security incident response team (CSIRT) a proactive approach to incident detection and response. Detailed views of incidents, incident triage, mitigation, eradication and remediation in real-time. Provides semi-automated and automated incident responses on security devices.