How to Create & Customize Correlation Rules on Logsign SIEM

If you have been using a SIEM tool for quite a time, you will know that it can turn out to be a powerful security tool, if appropriately deployed. In your organization’s network, network devices such as IDS/IPS, firewalls, and routers generate a plethora of log data. Like these devices, there are many sources of data for a SIEM solution. The first barrier a SIEM encounters is normalizing the log data before it can detect and alert your team.
If your SIEM solution is configured correctly, it will filter through irrelevant log data to allow your security team to focus on essential and high-risk alerts. Correlation rules play a crucial role in the configuration of a SIEM platform. In this article, we explore what correlation rules are and how you can create your organization-specific correlation rules on Logsign SIEM.
Your SIEM is continuously fed event logs from a large number of sources in your organization’s network. A correlation rule helps a SIEM solution in identifying which sequences of events would be an indication of anomalies to detect a security incident. For example, a correlation can be simply represented as:
When x happens, do y and username_r should be notified.
When either x or y happens, username_r should be notified.
When x and y along with z happen, username_r and username_s should be notified.
In a practical sense, a couple of examples of correlation rules can be:
While it cannot be denied that these correlation rules cannot be triggered by either honest mistakes or simple user errors, they are critical indicators of cyber attacks and must be assigned a high priority.
Your IT infrastructure will consist of different applications, software, network devices, and other hardware equipment. Each of these equipment will have their own format for recording log entries. Event logs from different sources will have different information fields and data formats. Ideally, a SIEM system is expected to parse these different log formats and normalize them in a standard format so that this data can be analyzed. Here, a SIEM platform attempts to universalize the log entries coming from a wide range of sources.
During the normalization process, a SIEM answers questions such as:
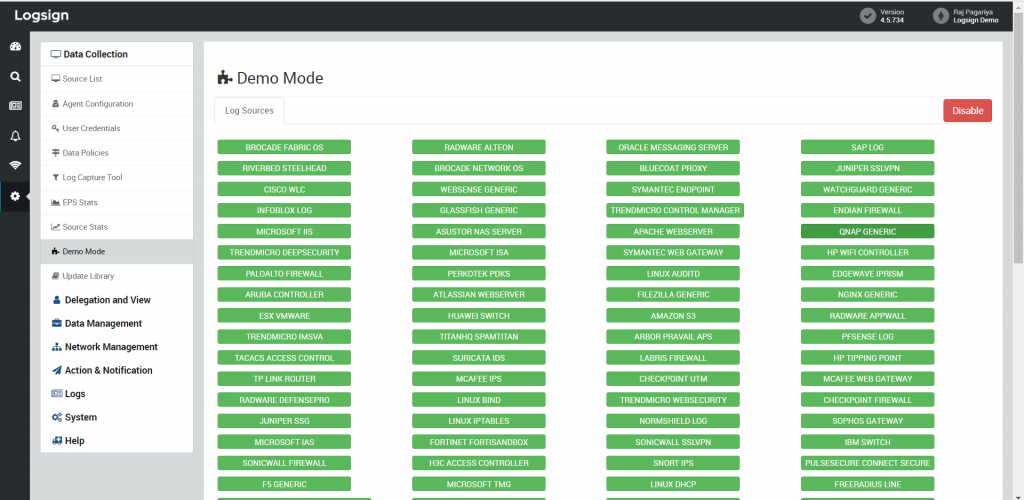
Figure 1: Some of the data sources on Logsign SIEM
Efficient normalization of log data can streamline the working of your correlation rules without any bottlenecks. As normalization for a SIEM platform improves, false positives decrease, and detection power increases. While Logsign SIEM normalizes log data after receiving it from the configured sources, you can further arrange data specific to your requirements while defining a new rule for a better presentation of data.
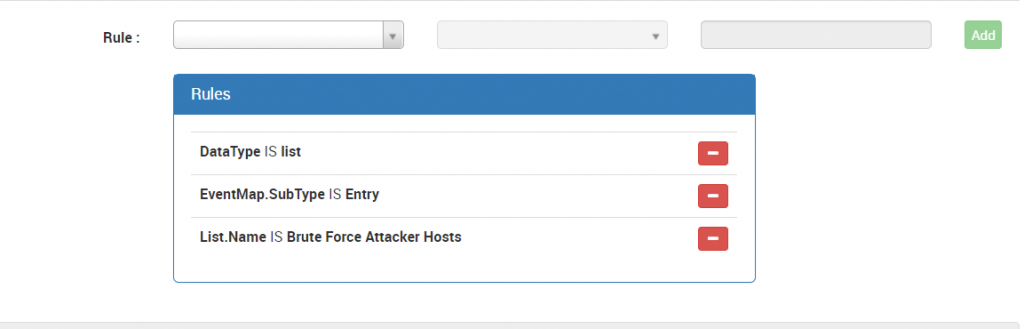
Figure 2: Data arrangement while defining a rule on Logsign SIEM
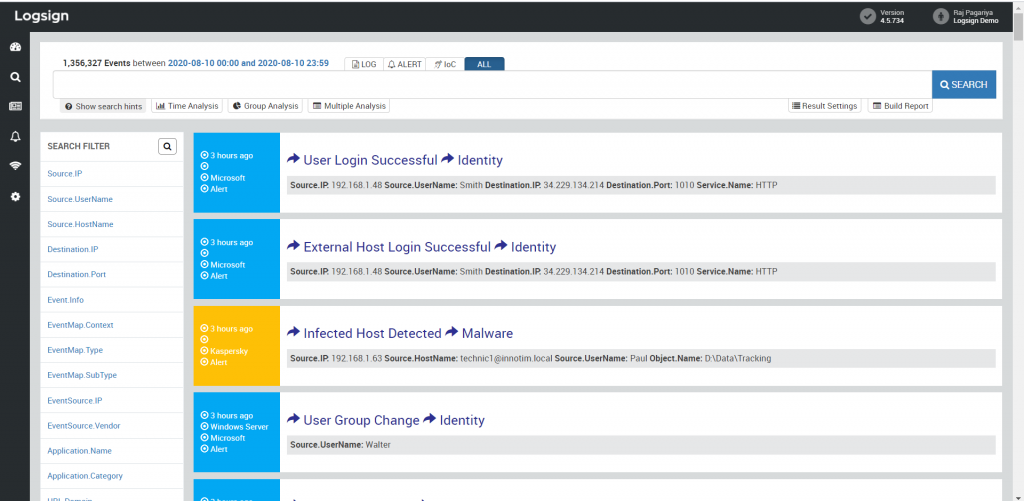
Figure 3: Log data from different sources presented universally after normalization on Logsign SIEM
Logsign SIEM already comes with inbuilt correlation rules that are continuously tested and updated by our internal teams. If you plan to create new correlation rules, you must ensure that your correlation rules don’t lead to your security team wasting their efforts to filter through false positive alerts. While it cannot be denied that it is impossible to have zero false positives in any SIEM solution, we often recommend our clients that your customizations should not increase the probability of false positives.
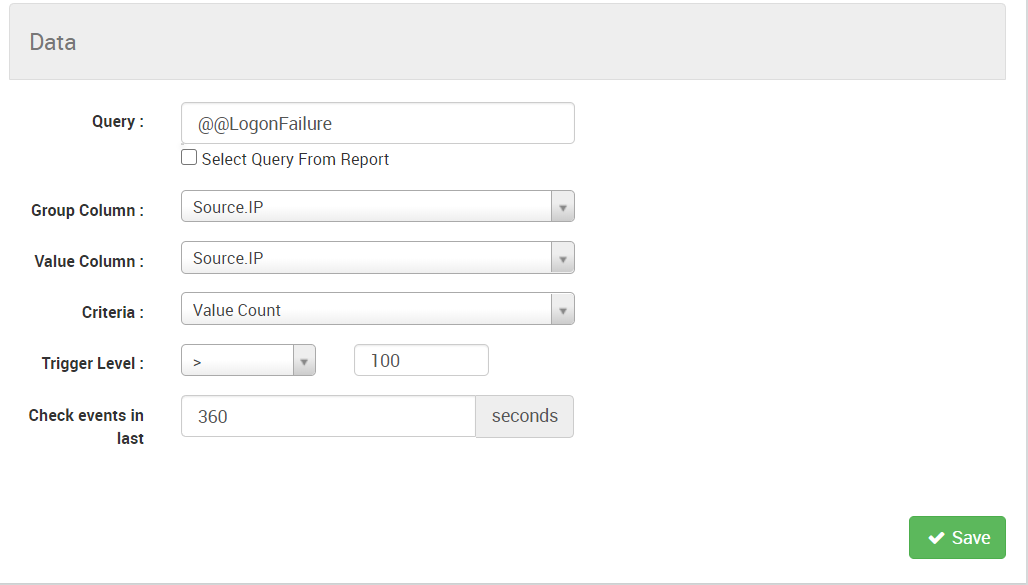
You will encounter correlation rules on Logsign SIEM primarily in the Alerts and Behaviours section. For example, this image shows how a series of logon failures are detected as an abnormal behaviour on Logsign SIEM.
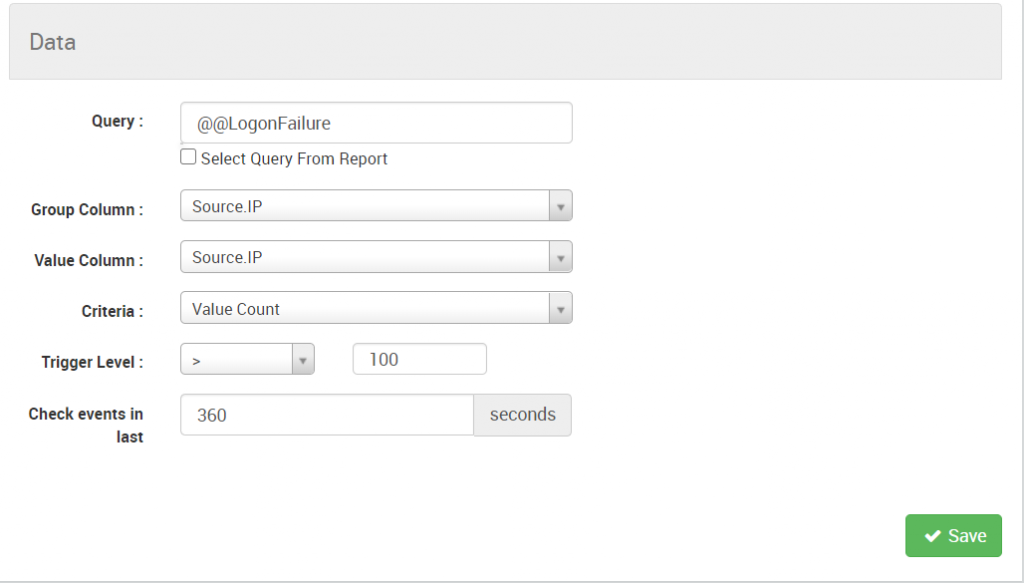
Figure 4: Correlation for login failure
Have you been able to create new correlation rules specific to your organization on Logsign SIEM? If not, what are the issues you are facing? Please let us know and get in touch with our support team anytime.