UBA vs UEBA - Decoding the Differences


One of the most important aspects of cybersecurity is monitoring and detecting threats that may compromise the security and integrity of your company. However, not all threats are easy to spot or prevent with traditional security tools.
That’s why many cybersecurity enthusiasts, professionals, and IT units of companies are curious about UBA and UEBA.
But what is the difference between UBA and UEBA? Let’s explore how they differ from each other and how they affect your cybersecurity posture.
User Behavior Analytics (UBA) is a cybersecurity solution that analyzes the behavior of users in a corporate network to detect anomalies that may indicate malicious activity.
Imagine if a user unexpectedly downloads a significant volume of data, accesses sensitive information, or logs in from an unfamiliar location or device. In such cases, UBA plays a vital role by diligently flagging these activities as suspicious.
This proactive approach allows UBA to promptly alert the dedicated security team, empowering them to swiftly take action and ensure the protection of valuable data.
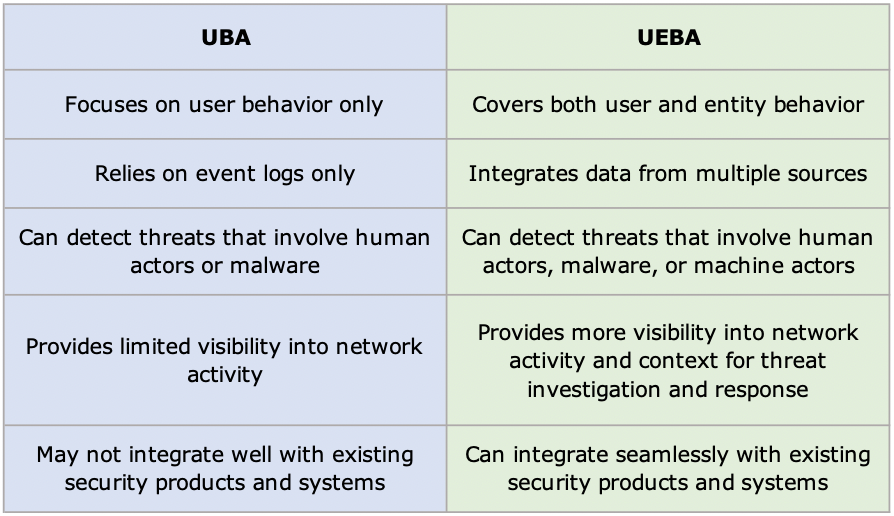
UBA can help detect insider threats, compromised credentials, data exfiltration, fraud, suspicious user types, and other types of attacks that directly involve human actors. However, UBA has some limitations that make it less effective in today’s complex and dynamic threat landscape.

User and entity behavior analytics (UEBA) is an extension of UBA that goes beyond analyzing user behavior to include the behavior of other entities in the network, such as devices, hosts, applications, and data repositories.
UEBA solutions recognize that not all threats involve human actors or malware. Some threats may originate from compromised or misconfigured devices, servers, routers, or endpoints that exhibit abnormal or malicious behavior.
UEBA works by collecting data on both user and entity activity from various sources across the network. It then uses machine learning to establish a baseline of normal behavior for each user and entity based on their behavioral biometrics, context, function, and patterns. It then creates risk scoring and compares the current behavior with the baseline to identify anomalies that may indicate a threat.
UEBA can help detect insider threats, compromised credentials, data exfiltration, fraud, malware-less attacks, advanced persistent threats (APTs), distributed denial-of-service (DDoS) attacks, and other types of attacks that involve both human and machine actors.
UEBA systems can also provide more visibility of the network activity and context for threat investigation and response.

UBA and UEBA share some common features and benefits, such as using automation to detect threats that may evade traditional security tools. However, they also have some key differences that make UEBA a more comprehensive and effective solution than UBA.
Here are some of the main differences between UBA and UEBA:

One of the benefits of UEBA over UBA is that it can integrate seamlessly with existing security products and systems.
This integration can enhance the data collection, analysis, and presentation capabilities of both UEBA and other security systems.
UBA, on the other hand, may not integrate well with existing security products and systems, as it relies on log data of security events only and may not be compatible with other data sources or formats. UBA may also generate false positives or miss some threats that involve non-human entities or complex patterns.
By integrating UEBA tools with other security systems, cyber security teams can also avoid duplication of efforts and reduce complexity and costs. By contrast, UBA may not offer the same level of integration and limit your visibility and real time detection capabilities.
Now that we know the features and scope of the two approaches, let's summarize the pros and cons of UBA and UEBA.
Imagine you are running a successful business in the digital world. You have a lot of data and customers to protect from cyber attacks. But you don’t have the time or resources to deal with multiple security tools and complex potential threats. You need a simple and effective solution that can handle everything for you.
That’s where Logsign UEBA comes in. Logsign UEBA is a part of the unified cybersecurity solution, Logsign Next-Gen SIEM, that gives you the best of both worlds: a powerful defense against cyber threats and a seamless user experience.
Logsign SIEM and UEBA work together to automatize incident response and management, analyze data for insights, and detect and prevent abnormal behaviors. With Logsign SIEM, you can rest assured that your business operations are always secure.
If this sounds like something you need, don’t hesitate to sign up for a live demo of Logsign SIEM today. You’ll be amazed by what it can do for you.