What Does a SIEM Solution Do: Logsign Perspective

Businesses are currently witnessing improvements in cybersecurity capabilities, thanks to advancements in Artificial Intelligence (AI). However, the progress is accompanied by a parallel increase in the threat and sophistication of cyber-attacks, especially when the right event monitoring and threat detection tools are not utilized.

Deloitte's latest research on security operations indicates that in 2023, 12.5% of businesses experienced more than one security event. So absolute security is a state of oblivion, and businesses must strive to achieve the maximum possible level of security.
The real challenge lies in investing in the right technologies to ensure that they are covered from all ends. To help you out, in this blog post, we'll take a look at security information and event management (SIEM) and Logsign's Unified Security Operations platform.
SIEM, short for security information and event management, represents the advancement of log management by integrating security event management (SEM) and security information management (SIM).
The SIM component gathers, processes, analyzes, and reports findings from log data. On the other hand, the SEM component operates in real-time to offer threat monitoring, event correlation, and incident response capabilities.
According to Gartner, SIEM is a technology that supports threat detection, compliance, and security incident management. It achieves this through the collection and analysis of security events, encompassing both near real-time and historical data, as well as a diverse range of other event data and contextual data sources.
SIEM security solutions have paramount importance for any organization’s security endeavor. A SIEM system responds quickly to security incidents and events to mitigate the impact of such attacks and safeguard organizations from the colossal damage of data breaches.
Therefore, effective and efficient SIEM systems can prevent notorious cyber-attacks, such as Ransomware attacks, as well as reputational damage to organizations.
A SIEM solution aggregates log data generated throughout your organization’s IT infrastructure, from applications to the network to security devices and host systems. After collecting and analyzing log data, the solution identifies security incidents and events.
Two primary objectives of a SIEM solution are:
Threat Detection: It provides reports on security-related events and incidents, ensuring your organization meets security requirements. Examples include failed logins, malware activity, possible malicious activity, and login attempts.
Incidence Response: It sends alerts if an activity is detected as a potential security issue, such as lateral movement within the network. By employing event correlation and advanced analytics, SIEM solutions enable the proactive identification of threats.
SIEM tools are versatile and context-dependent solutions that can be customized according to business requirements. These solutions can also be streamlined with other security tools and upgraded with additional packs that offer solutions for specific needs.
This means a SIEM tool can manage much more complicated tasks than you need. So how do these tools function? To answer this question, let’s take a look at the SIEM tool within Logsign’s Unified Security Operations platform.
Here are the basics of the Logsign SIEM:
Data Collection: The solution collects data from various sources within an organization's technical infrastructure, ensuring comprehensive visibility.
Security Data Aggregation and Normalization: Collected data is aggregated and normalized to ensure accurate and organized information for analysis.
Threat Detection and Analysis: Data analysis is used to detect and discover threats, leveraging AI-powered algorithms and advanced analytics. This enables security analysts to interpret log data effectively.
Customizable Alert Rules: Organizations can configure alert rules based on their security preferences. Logsign SIEM offers built-in alert rules that can be customized or expanded upon as per specific requirements.
Real-Time Notifications: Organizations can configure notifications to be sent to security teams whenever a security event or incident is detected. Logsign SIEM supports notifications through emails and SMS using different templates.
Advanced Search Functionality: This SIEM solution facilitates advanced search features, enabling security experts to efficiently search through collected data. Time analysis and group analysis features further enhance the search capabilities.
Defining Abnormal Behavior: Logsign’s SIEM solution allows the definition of abnormal behavior of assets and users, enabling the detection of unusual activities or potential threats.
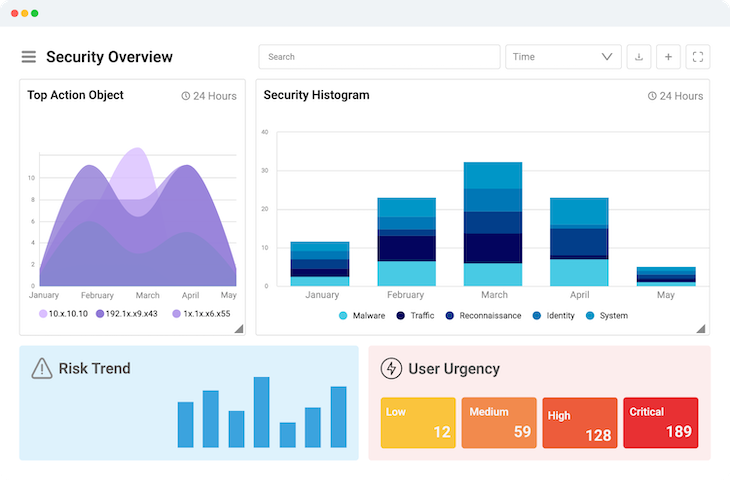
Interactive Dashboards: Logsign’s SIEM solution provides a single-pane view of an organization's security posture through interactive dashboards. It offers a range of pre-built dashboards across more than 10 categories, with the flexibility to create custom dashboards.
Comprehensive Reporting: Logsign’s solution enables the generation of different types of reports to meet compliance and management needs. It offers over 100 types of reports that can be exported in XML, HTML, and PDF formats.
When choosing a SIEM tool for your organization, it's crucial to consider certain factors that will ensure the effectiveness and suitability of the solution. Here are some key aspects to look for in a SIEM solution:

A robust security information and event management solution should offer advanced log analysis benefits and capabilities, enabling deep inspection of log data from various sources.
Look for a solution that can efficiently process and correlate events in real time, allowing for swift detection and response to security incidents. By analyzing logs from diverse systems and applications, the solution should provide valuable insights into potential threats and anomalous activities.
A SIEM solution should employ intelligent algorithms to detect and prioritize threats accurately. The system must have an enhanced Threat Detection capability that empowers your security defense through early detection and automated response.
Once the threat is detected with the automated active response, the SIEM should remediate it with pre-programmed corrective actions. Additionally, the solution should help address and manage the aftermath of a cyber-attack or security breach.
Compliance requirements, such as GDPR and PCI DSS, are crucial considerations for organizations. Ensure that the solution you choose offers specific SIEM GDPR compliance modules and reporting capabilities to meet regulatory standards.
Opt for SIEM features such as pre-built compliance reports, customizable compliance rules, and the ability to generate audit-ready reports effortlessly.
As your organization grows, your solution should be able to scale seamlessly to accommodate increasing data volumes and evolving security needs.
A solution that provides flexible deployment options, including on-premises or hybrid models, can provide scalability that ensures the solution's longevity and adaptability to future requirements.
A user-friendly interface that allows security analysts and teams to navigate and operate efficiently is essential.
Look for intuitive dashboards that provide a single-pane view of your organization's security posture, with customizable widgets and visualizations. This allows for easy monitoring, quick insights, and effective management of security events.
A SIEM solution should provide comprehensive reporting capabilities to enable decision making, measure security posture, and demonstrate compliance.
Customizable reporting features allow you to create tailored reports specific to your organization's needs. Advanced analytics capabilities, such as data visualization and trend analysis, can provide valuable insights into security patterns and enhance proactive threat detection.
Choosing the right SIEM solution requires careful evaluation of the above factors to ensure it aligns with your organization's security objectives and operational requirements. To guarantee cyber resilience of your business, you need a comprehensive solution that extends beyond SIEM capabilities.
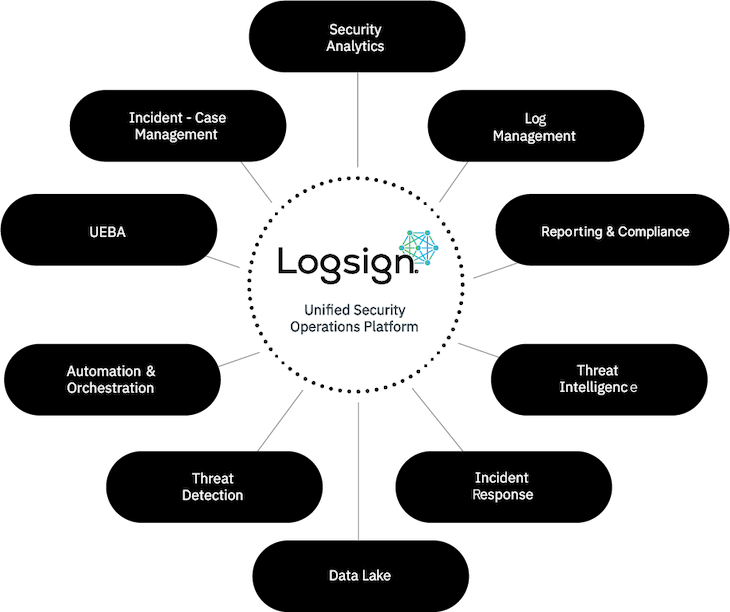
That's where Logsign comes in. We are committed to excellence, and our flagship product, the Unified Security Operations platform, reflects our dedication to delivering intelligent, user-friendly, and cost-effective cybersecurity detection and response solutions.
By choosing Logsign's Unified SO Platform, you are not only investing in a product but also embracing a promise – a promise of unwavering security.
Our Unified Security Operations platform seamlessly integrates Threat Intelligence (TI) with a comprehensive suite of security operation tools, including Security Information and Event Management (SIEM), User Entity Behaviour Analytics (UEBA), and Threat Detection, Investigation, and Response (TDIR).
This platform simplifies the deployment and management of multiple cybersecurity tools, streamlining the entire process and making it highly efficient.
With an intuitive interface, effortless deployment, powerful search functionality, and transparent pricing, Logsign simplifies the cybersecurity landscape, providing a smooth and stress-free solution for your security requirements.
Take the first step towards a digitally safer and more secure future by reaching out to us today!