The Importance and Difference Between Indicators of Attack and Indicators of Compromise

In the forensic world, an IoC is an evidence on any computing machine such as a computer, laptop, mobile, and so on. The IoC indicates that the security of the network has been compromised. They can be collected from the operating system, network, memory, and so forth. The IoC can be a filename, log file, a registry key, a hardcoded IP address, or an MD5 hash.
Investigators or forensic analysts gather these data artifacts at the request of the affected organization or individual. Investigators can be either company’s own employees or outsourcers. The collected data is used to detect a potential incident and quarantine malicious files to prevent attack escalation and terminate it completely.
It is important to note that IoC is based on a reactive approach used to track threat actors. Hence, when an IoC is found on the computer, there is a great probability that such a system has already been breached.
According to McAfee, a cybersecurity firm, the IoA is a unique construction of the unknown attributes, IoC, and contextual information, including organizational risk and intelligence, into a dynamic, situational picture that helps to prepare response strategies.
What would be your response if you find something suspicious outside your home or office? For example, if someone is breaking into your home, you might call the police immediately. Likewise, if you see the fire, you might call the fire brigade. However, if this fire is through Café’s window, you may not take any action because a chef might be cooking something.
In the above examples, we can observe that what is suspicious and what is benign. The examples of home and fire provide us a baseline of “what is normal” and “what is abnormal.” We can also understand the “Context” through these examples. For instance, Context is defined as “when, what, who, and where.” Another two important contexts – namely “how and why” are based on investigators’ viewpoint. Based on Context, we would take a decision. For example, how to deal with a thief who was breaking into the house and fire that was seen through the window.
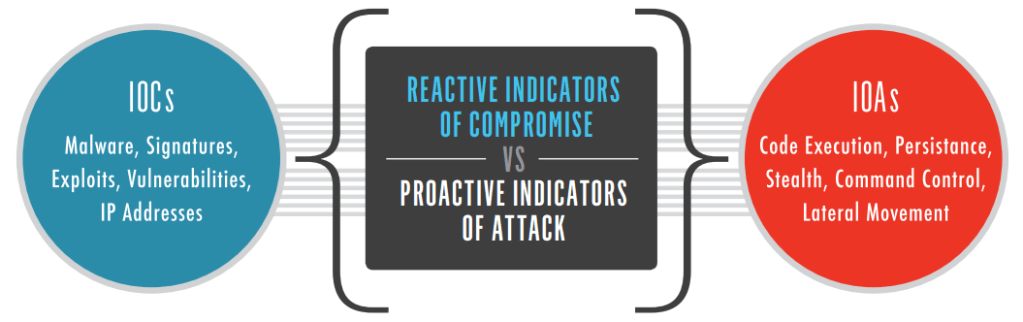
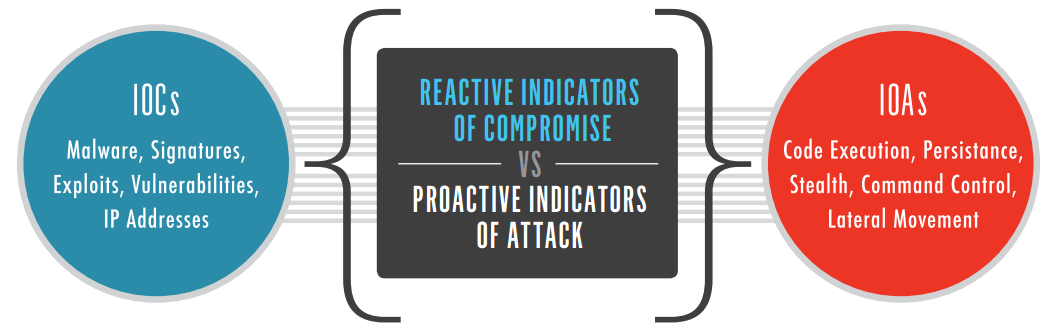
IOCs Vs IOAs
Source: CROWDSTRIKE
Typically, an IoA involves contextual attributes that we have discussed in the previous section. We only consider IoA as bad based on what they mean to us and the situation. In the following sections, we will take a deep look into the difference between the IoC and IoA.
The IoC is based on the reactive approach because it indicates that the attack has already been made. In fact, reactive approaches execute in the aftermath of an attack. For example, you will identify the presence of viruses, malware, exploits, signature, malicious IPs that are left behind by the breach.
Contrarily, IoA represents a proactive approach (just like Threat Hunting) in which defenders look for the early warning signs that can indicate an attack but it is not always true. From an information security perspective, warning signs can be either true or false positive, code execution, Stealth, Command and Control or lateral movement within networks.
We can understand the difference in simple words. For example, reaching the crime scene after the occurrence of the incident or crime (reactive and IoC) and reaching the potential crime scene before the occurrence of the incident (proactive and IoA). In later, we can prevent the occurrence of the incident because the crime has not been taken place so far.
An IoC provides us the information about known adversaries. In other words, using IoC, we can identify who is involved in the attack. On the other hand, an IoA provides us the contextual information whereby the attack can be either suspicious or benign. If it is benign, then there is no adversary.
Let us consider that robbers break into the bank and loot all money. Forensic investigators reach the crime scene and collect evidence. After watching the videos of CCTV cameras, investigators discover that the robbers were wearing black caps and white face masks. In addition, they were driving the red van. This is known as IoC. Using these IoC, investigators can lead to criminals.
What happens when the same robbers change their tactics in the next robbery? For example, they wear blue hats and purple face masks, as well as use bikes rather than a red van. In this case, there is a high probability that another robbery would take place because the vigilance or security team relies on IoC that reflects the outdated information.
Instead of IoC, if the surveillance team had been using IoA, then the situation would have been quite different. For instance, a smart robber, first and foremost, would chase the bank, perform reconnaissance, and understands defensive vulnerabilities. He would penetrate the bank when the time and situation is favorable. After that, a thief would disable the security alarms, approach the vault, and attempts to open it. These are all behaviors or IoA, rather than IoC. If the surveillance team detects these IoA, the attempt of robbery can be foiled and no robber can escape the bank’s premises.
Based on the above discussion, we can say that IoA is more effective than IoC. However, we cannot underestimate the significance of IoC because they have their own unique benefits.
The organization can deploy a Security Information and Event Management (SIEM) solution to aggregate log entries from across the network into a single database and use that database for known IoC. Use the next-generation Logsign SIEM tools to collect known IoC. Likewise, Security Orchestration, Automation, and Response (SOAR) tool enable security professionals to gain attacker insights with threat rules derived from the insight into attacker’s Tactics, Techniques, and Procedures (TTP) as well as known IoC. To do this, SOAR tools utilizes multiple Threat Intelligence Feeds (TIFs). You can use the Logsign SOAR tool to perform this function.
Though threat actors are very sophisticated nowadays, you can use even more sophisticated techniques and approaches to counter these notorious adversaries. To this end, using the IoC and IoA is helpful. The IoA is more effective than IoC. In fact, IoA is based on behaviors or contextual situations that are more reliable. Using SIEM or/and SOAR tools can be very effective for both IoC and IoA. SOAR can automate various functions and reduces the involvement of manpower.