What is UEBA: The Complete Guide to User and Entity Behavior Analytics


As the world becomes increasingly digital, cyber-attacks are becoming more sophisticated, and traditional security measures, like firewalls and passwords, are no longer sufficient in protecting sensitive data.
This raises a critical question: how can organizations identify hidden threats lurking within their networks? While traditional security analytics solutions can miss these hidden threats, UEBA emerges as a promising tool that uses AI to monitor user behavior anomalies and flag the ones that might indicate a cyberattack.
In this comprehensive guide, we'll break down UEBA, how it works, and why it's crucial for an organization's cybersecurity.
UEBA, or User and Entity Behavior Analytics, is a powerful cybersecurity behavior analysis tool that uses ML and statistical analysis to create a comprehensive understanding of activity within your network.
UEBA tools can flag anything from unauthorized access attempts by compromised accounts to unusual data transfers that could signal exfiltration attempts or malware infections.
Here are the key benefits of UEBA:
In essence, UEBA technology acts as a proactive guardian and provides constant cybersecurity monitoring for anomaly detection for entities that traditional security measures might miss. UEBA solutions not only provide user activity analysis but can analyze the behavior of devices, applications, and even data itself.
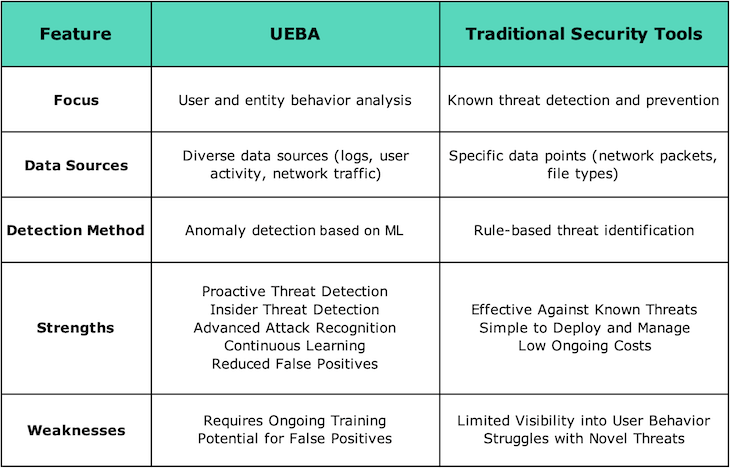
While traditional security tools remain fundamental to cybersecurity, they often treat authorized user actions as routine. The technology of user behavior analytics brings a new level of insight by focusing on behavior patterns.
This comparative table illustrates the importance of User and Entity Behavior Analytics:
UEBA is capable of identifying unauthorized attempts, an excessive number of failed logins, or an authorized user login from an unfamiliar device or location as suspicious behavior. It prevents attackers from gaining system access via phishing or stolen credentials and enhances the overall robustness of cybersecurity measures.
While they may seem to serve similar purposes, SIEM and UEBA are two critical tools in any security professional's arsenal. When used together, they excel in providing a comprehensive view of network activity.
SIEM provides raw data from various sources, which is enriched by UEBA with contextual information and behavioral insights. SIEM's rules and correlations help identify known threats, while UEBA's ML and statistical models detect unknown or emerging threats through entity behavior monitoring and entity risk management.

SIEM alerts cybersecurity teams about security issues and supports forensic analysis and compliance through log management. UEBA generates user risk profiling scores to prioritize investigations and aids in root cause analysis by providing user profiles.
Both systems monitor for suspicious user types, with SIEM focusing on excessive data access and unauthorized logins, and UEBA detecting abnormal behaviors and signs of manipulation through predictive analytics in security.
Implementing UEBA deployment strategies demands thorough planning and integration with existing security setups. Following best practices for UEBA implementation ensures an advanced threat detection and response to cybersecurity needs.
Here are tips for successful UEBA integration:
The first step is to clearly define what you want to achieve with UEBA. You can start by identifying the specific areas you're most concerned about, such as insider threat detection, advanced malware infections, or unauthorized access attempts. Identify key data sources for analysis, such as user activity logs, network traffic, file access logs, and email communications.
When choosing a UEBA vendor, consider the following:
The next critical step is establishing data collection processes. Configure data pipelines to gather information from your identified sources and ensure its quality before feeding it into the UEBA system. Data inconsistencies or errors can significantly hinder the effectiveness of anomaly detection. Data normalization and cleansing techniques might be necessary to prepare your data for analysis.
Allow the UEBA system sufficient time to analyze historical data and establish baseline behavior patterns for users and entities within your network. This process involves behavioral analytics for security, where the UEBA system analyzes user and entity actions to identify patterns and establish what constitutes normal behavior.

During this initial period, it's crucial to monitor the system's performance and fine-tune detection rules, including security event correlation, to minimize false positives. Expect this stage to be iterative, requiring adjustments as the system learns and refines its understanding of normal activity.
UEBA is not a "set it and forget it" solution. Maintenance is essential in security monitoring solutions to ensure its effectiveness. Regularly review the system's performance metrics, such as the number of alerts generated and their accuracy.
As user behavior monitoring evolves, adjust baselines accordingly to maintain optimal detection capabilities. Refine detection rules based on real-world security incidents and threat intelligence feeds to ensure the system stays up-to-date with the latest attack methods.
For a successful UEBA implementation, integrate the chosen solution with existing security tools to foster a unified security posture. This will streamline workflows and allow the security team to leverage the insights generated by UEBA alongside data from other security solutions. Train the security team on interpreting UEBA alerts and effectively responding to potential security incidents identified by the system.
Scaling UEBA for enterprise security is crucial for growing organizations looking to bolster their cybersecurity defenses. While traditionally associated with large enterprises, UEBA for small businesses is becoming increasingly relevant as these organizations face similar security challenges but often lack the resources of their larger counterparts.
Through security event monitoring and behavioral profiling for entities, implementing a UEBA solution helps all sizes of organizations to enhance their security posture. It offers scalable security across multiple networks and helps organizations to excel in cyber threat intelligence.
Here are some industries benefiting from UEBA:
Banking & Finance: UEBA excels in security incident detection and can help detect fraudulent transactions, insider threats attempting to steal data, and sophisticated malware designed to infiltrate financial systems.
Retail: UEBA can be instrumental in identifying fraudulent purchases, account takeovers, and attempts to steal customer information through security data analysis.
Manufacturing: UEBA can monitor activity within industrial control systems, helping to detect unauthorized access, manipulations aimed at disrupting operations, and potential cyberattacks.
Healthcare: UEBA can monitor user activity within healthcare systems, helping to identify access attempts, potential data breaches, and even insider attempts to tamper with patient records.
Government: UEBA can be crucial for detecting unauthorized access attempts, data exfiltration efforts, and insider threats aiming to compromise classified information. UEBA vs threat intelligence demonstrates the system's ability to not only leverage existing threat knowledge but also uncover unknown threats through behavioral analysis.
Education: UEBA can help detect suspicious activity within educational networks, such as unauthorized access attempts to student records or attempts to disrupt online learning platforms.
Logsign's Unified SecOps Platform signifies a paradigm shift in cybersecurity, driven by innovation and a deep understanding of evolving threats. At its core lies groundbreaking User and Entity Behavior Analytics (UEBA) functionality, integrating advanced tools like Security Information and Event Management (SIEM), Threat Intelligence, and Threat Detection, Investigation, and Response (TDIR).
Here are the key benefits of Logsign's Unified SecOps Platform
This seamless integration offers security teams a comprehensive view of their organization's security posture, empowering them to identify and mitigate threats proactively.
Logsign, a trusted cybersecurity partner, provides a Unified SecOps Platform that features a revolutionary approach to UEBA. Logsign UEBA employs a multi-step process to detect and prioritize security threats. It gathers data from a variety of sources including logs, network traffic, endpoints, cloud services, behavioral patterns, and threat intelligence feeds to establish standard behavior patterns for users and entities.
Logsign UEBA aligns the analyzed behavior with the globally-accepted MITRE ATT&CK framework, which is a comprehensive database of adversary tactics and techniques. It flags potential malicious activities by detecting deviations from the usual behavior. This includes abnormal use of tools, connections to malicious domains, and indicators of system compromise.
Logsign UEBA also ranks alerts based on the severity and risk level of the detected anomalies. It further provides contextual details about the involved user or entity, such as their role, location, and device type. This aids in understanding the extent and implications of the incident, and guides suitable actions for containment.
In conclusion, UEBA represents a significant advancement in cybersecurity, offering an intelligent and proactive approach to detecting and responding to threats.
Its focus on behavior patterns and anomaly detection makes it a powerful tool for uncovering hidden threats that traditional security measures might miss.
As cyber threats continue to evolve, Unified SecOps Platforms that seamlessly integrate with UEBA will become increasingly indispensable in maintaining robust cybersecurity defenses.